This article is part of a series of 4 where I am talking about how to setup site-2-site VPN between on-premises and Azure using Tomato Shibby Mod, Entware-ng and Strongswan. For a better understanding please make sure you read also the other parts:
- Install and configure Entware-ng + strongSwan on your router.
- Configure and perform the site-2-site VPN using Azure dynamic gateway.
- Configure and perform the site-2-site VPN using Azure static gateway.
- Troubleshooting Azure site-2-site VPN and strongSwan.
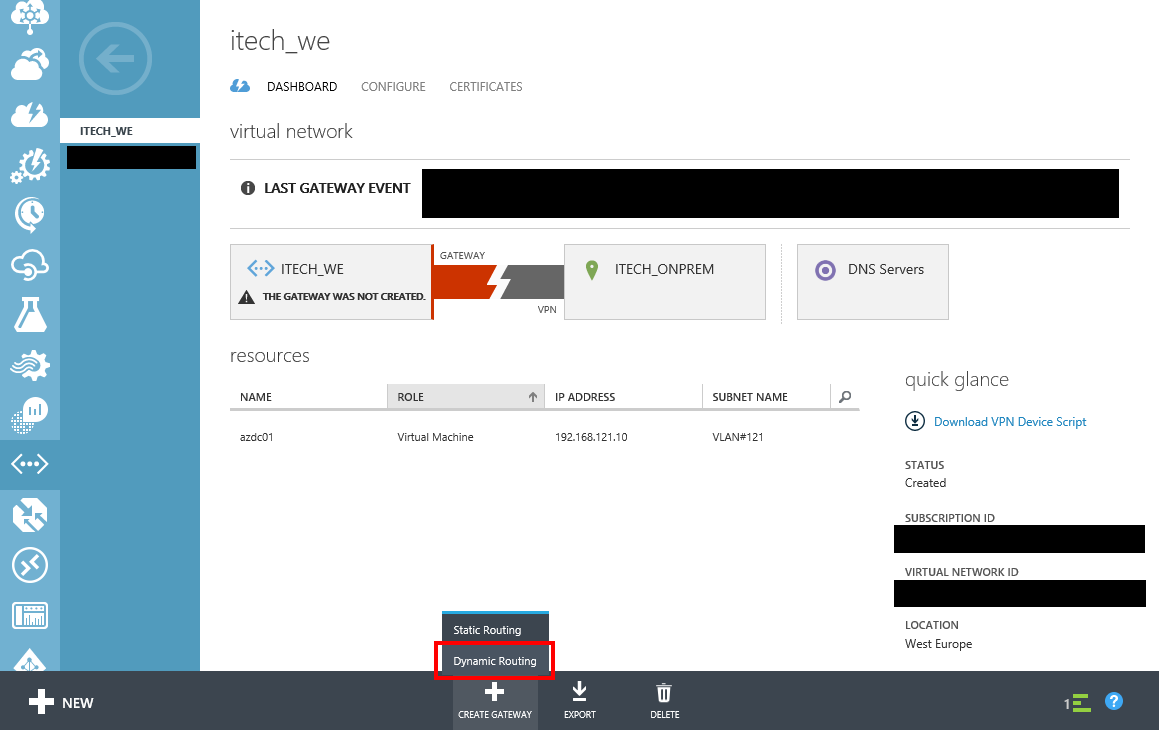
Configure and perform the site-2-site VPN using Azure dynamic gateway
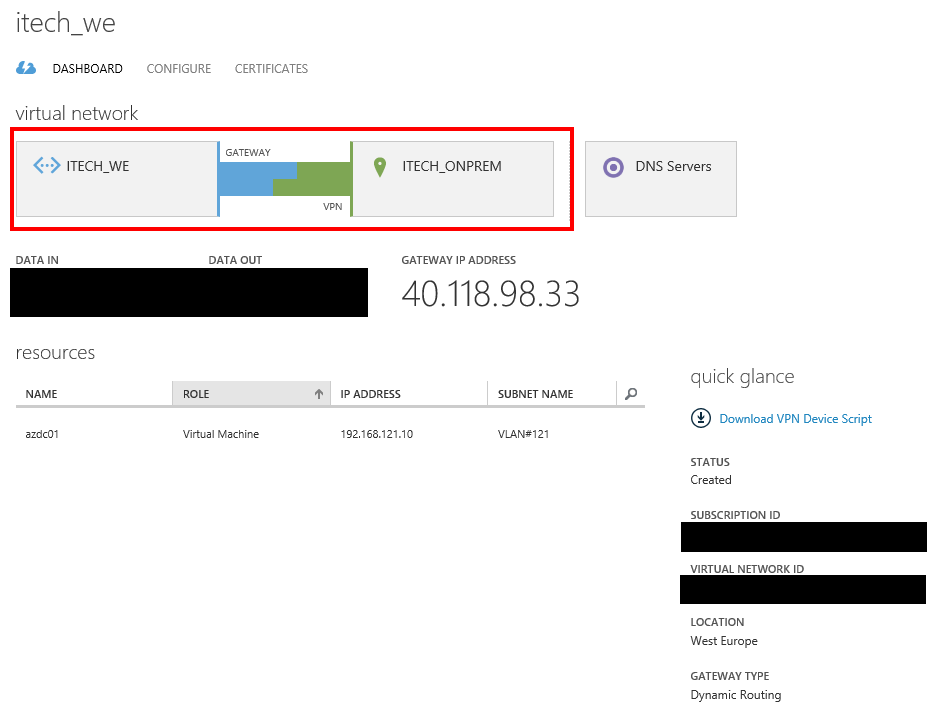
In the Azure Portal, carefully select Dynamic Routing when the VPN gateway creation is initiated.
In this example:
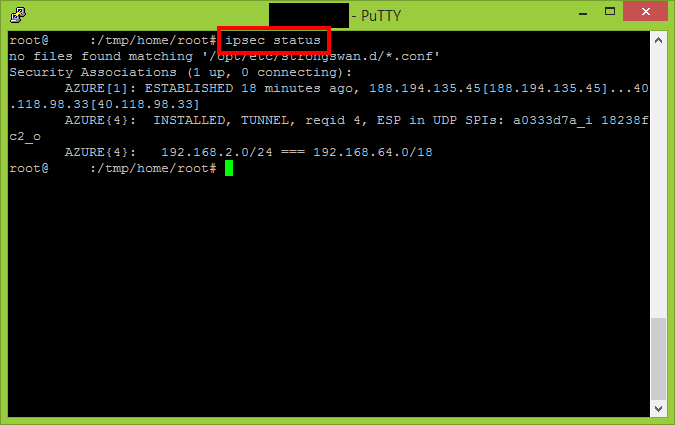
- 188.194.135.45 represents the on-premises gateway IP address (the router configured with Entware-ng + strongSwan)
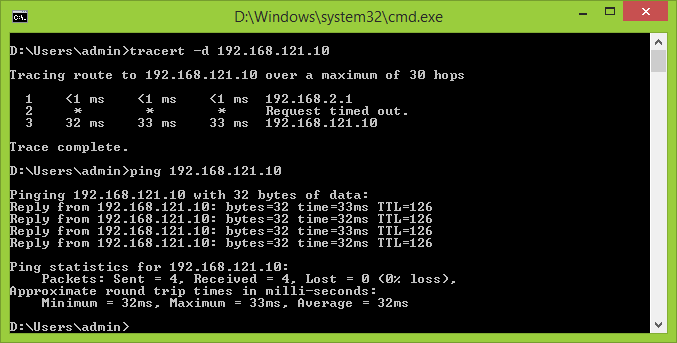
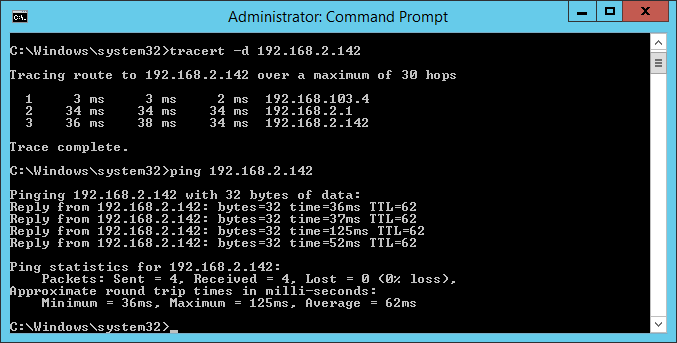
- 192.168.2.0/24 represents the on-premises network subnet
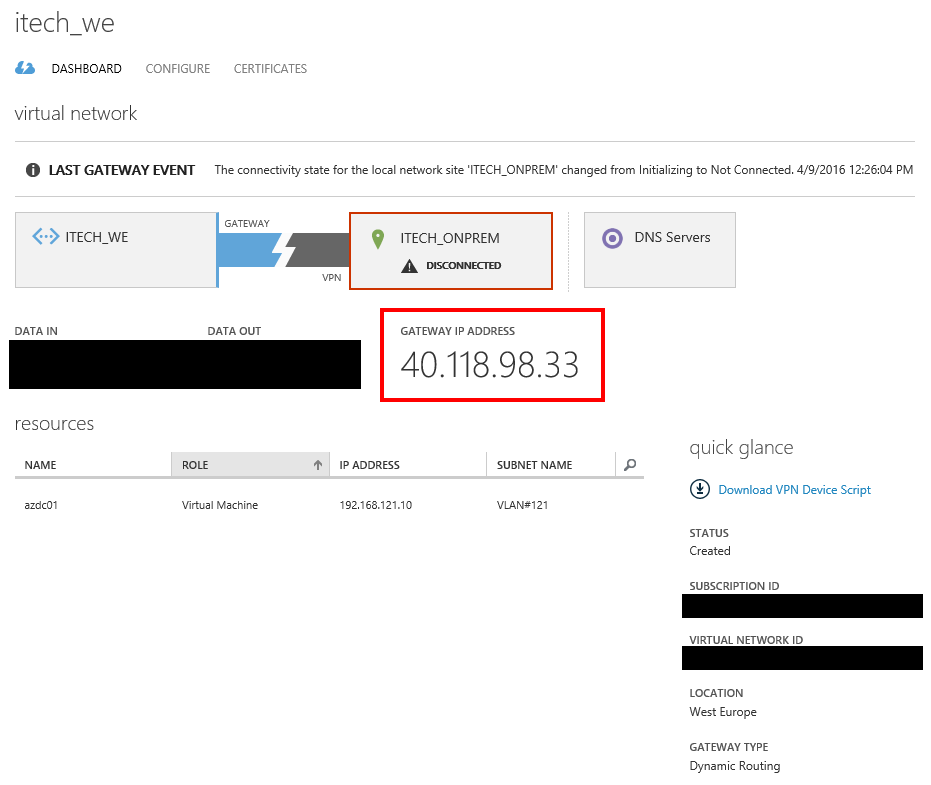
- 40.118.98.33 represents the Azure VPN gateway IP address
- 192.168.64.0/18 represents the Azure network subnet
- “eU3V1TugtEQOMSqQYemNtH7yRb8c6mta” represents the pre-shared key
Connect to your router and make the following adjustments to your ipsec.conf and ipsec.secrets files.
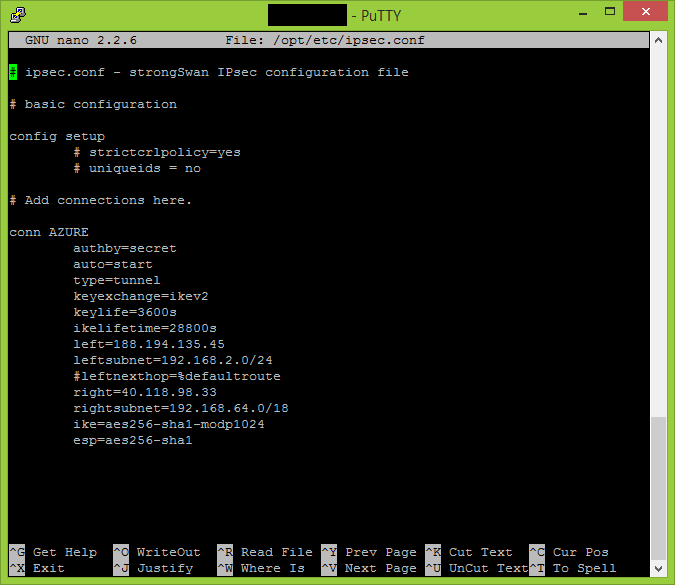
nano /opt/etc/ipsec.conf
# ipsec.conf - strongSwan IPsec configuration file
# basic configuration
config setup
# strictcrlpolicy=yes
# uniqueids = no
# Add connections here.
conn AZURE
authby=secret
auto=start
type=tunnel
keyexchange=ikev2
keylife=3600s
ikelifetime=28800s
left=188.194.135.45 #IP address of your on-premises gateway
leftsubnet=192.168.2.0/24 #network subnet located on-premises
#leftnexthop=%defaultroute
right=40.118.98.33 #Azure VPN gateway IP address
rightsubnet=192.168.64.0/18 #Azure network subnet defined in cloud
ike=aes256-sha1-modp1024
esp=aes256-sha1
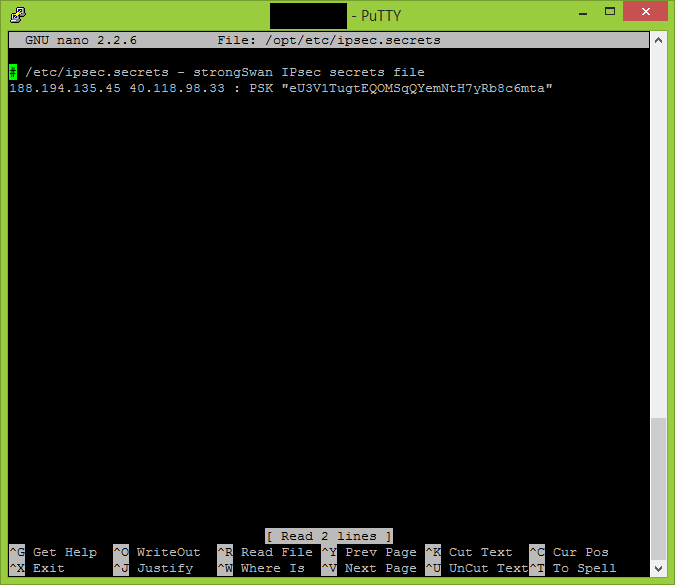
nano /opt/etc/ipsec.secrets
# /etc/ipsec.secrets - strongSwan IPsec secrets file 188.194.135.45 40.118.98.33 : PSK "eU3V1TugtEQOMSqQYemNtH7yRb8c6mta"
Please note any additional empty new line or invalid characters added to these two configuration files can lead to unsuccessful VPN site-2-site.
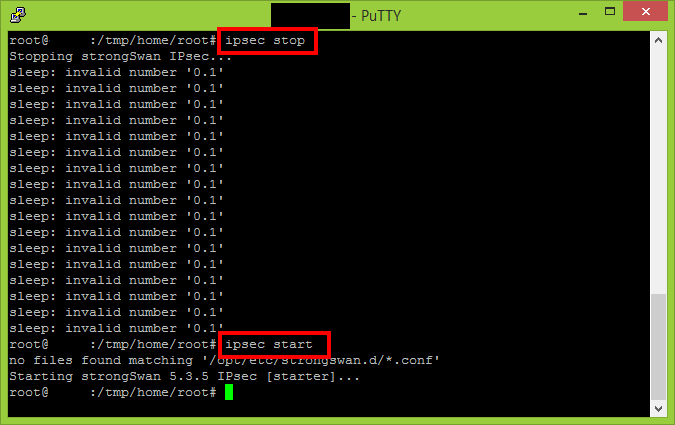
Execute the following two commands to ensure the new settings are propagated.
ipsec stop ipsec start
Use the “status” parameter to see if the VPN connection has been established.
ipsec status
After couple of minutes the connected status will be reflected also in the Azure Portal.
By default your router will allow all outbound traffic with your defined Azure networks, but will block all the traffic initiated to your on-premises subnet. That’s why is necessary to open additional traffic between the two internal networks (on-premises and Azure).
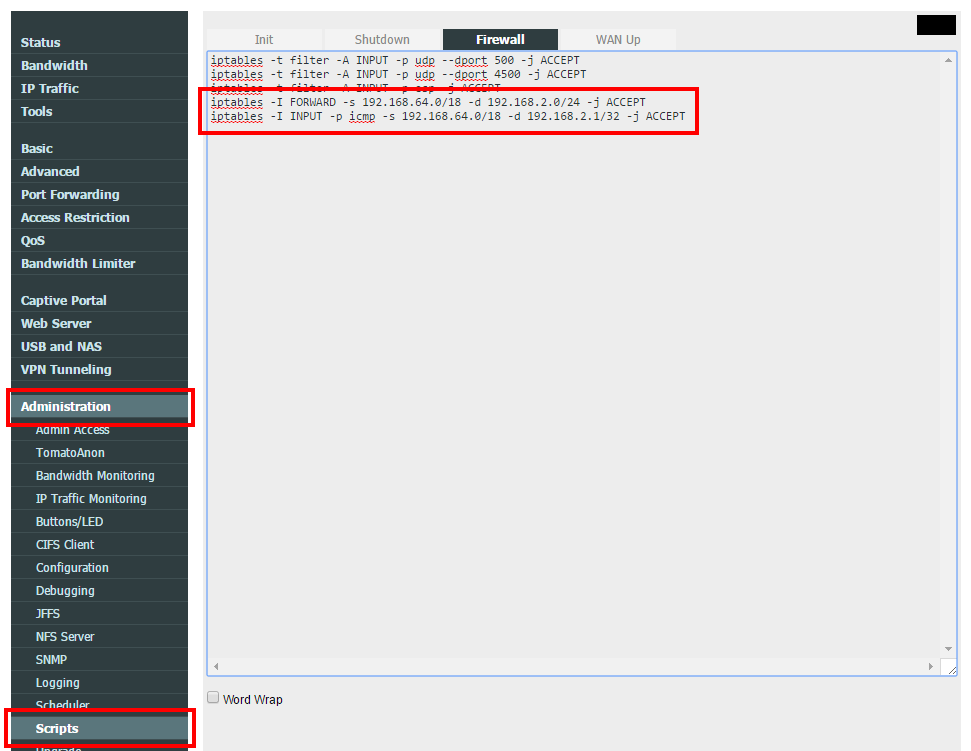
Append the following commands in the Firewall script section. Please keep in mind is necessary to call/execute these commands also in the SSH session in case is necessary to make the changes immediately.
iptables -I FORWARD -s 192.168.64.0/18 -d 192.168.2.0/24 -j ACCEPT iptables -I INPUT -p icmp -s 192.168.64.0/18 -d 192.168.2.1/32 -j ACCEPT
Let’s test the site-2-site connectivity.
From on-premises to Azure.
From Azure to on-premises.
Continue with On-Premises Site 2 Site VPN with Azure using Tomato Shibby Mod (Entware-ng and Strongswan setup) – part 3.