This post is much more as an update for the “next-next-finish” approach of setting up a TLS/SSL site, or Microsoft Internal Certificate Authority.
It started months in the past and if you didn’t implement the fixes yet, at least is good to be aware of:
- Gradually sunsetting SHA-1
- SSL 3 is dead, killed by the POODLE attack
- RC4 in TLS is Broken: Now What?
- Perfect Forward Secrecy & Forward secrecy (Wikipedia)
- If you have a fresh new Windows Server 2012 R2 and you setup an internal Certificate Authority it will by default be configured to use SHA1! Don’t resume to next-next-finish setup.
- If you already have an internal Certificate Authority, most likely is using SHA1. It is recommended to change it.
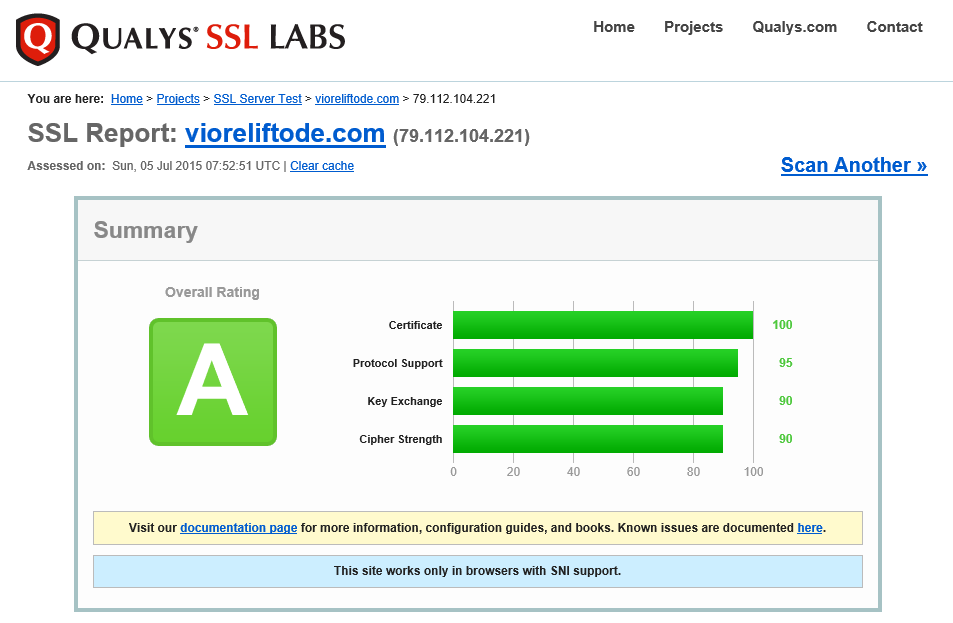
1. If you have a TLS/SSL web site, verify now your overall rating on SSL LABS.
In case you are not rated to A, then the following article will for sure get you there – https://www.hass.de/content/setup-your-iis-ssl-perfect-forward-secrecy-and-tls-12 (the article is well written and the basic explanation is provided). Follow the article, or simply execute the PowerShell script.
How vioreliftode.com is rated after the changes?
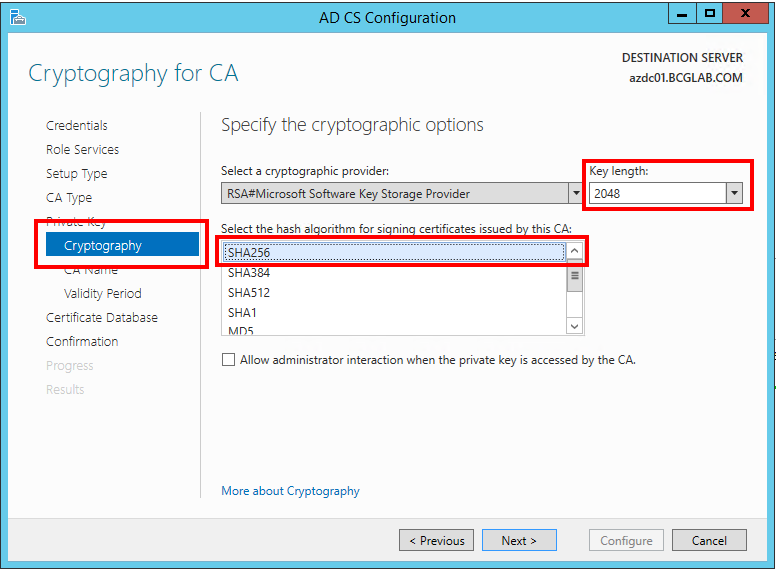
2. If you have a fresh new Windows Server 2012 R2 and you setup an internal Certificate Authority make sure during the setup (in the Cryptography for CA section) you select SHA256 as hashing algorithm and minimum 2048 for the key length. As mentioned above, by default the wizard is configured to use SHA1 -> DON’T use it anymore!
3. If you already have an internal Certificate Authority, most likely is using SHA1. It is recommended to change it. This is not difficult at all.
http://blogs.technet.com/b/pki/archive/2013/09/19/upgrade-certification-authority-to-sha256.aspx
http://www.cusoon.fr/update-microsoft-certificate-authorities-to-use-the-sha-2-hashing-algorithm-2
http://windowsitpro.com/security/your-organization-using-sha-1-ssl-certificates
As an update to the above articles – it is not mandatory or critical to renew your Certification Authority Certificate Root. The CA root can still stay SHA1, what is important is the new certificates your CA is issuing to be SHA256.