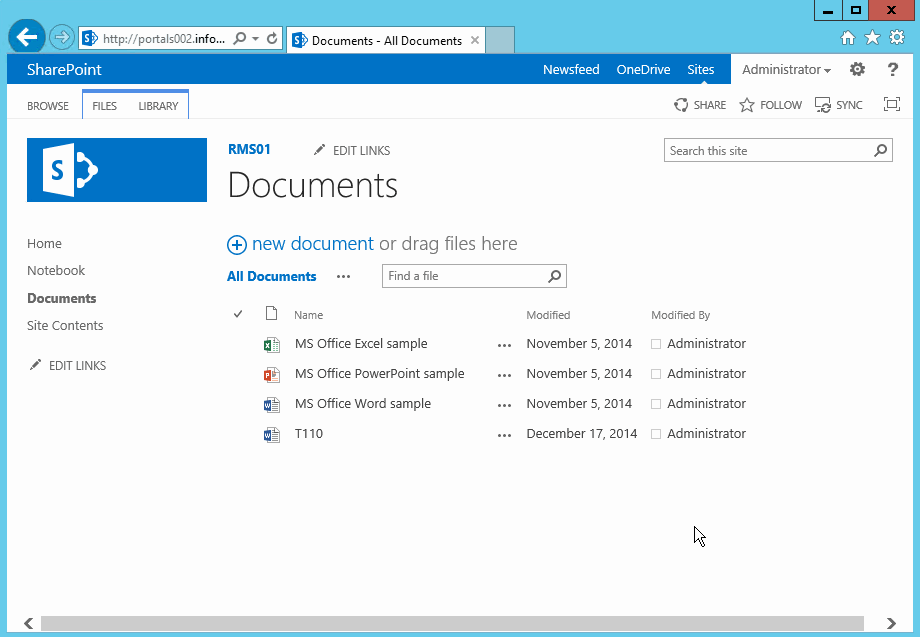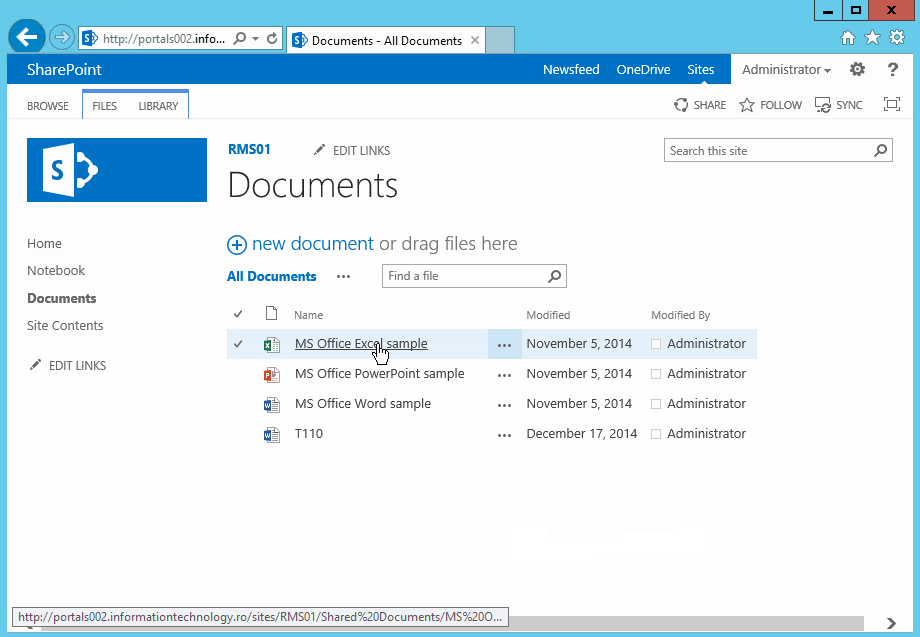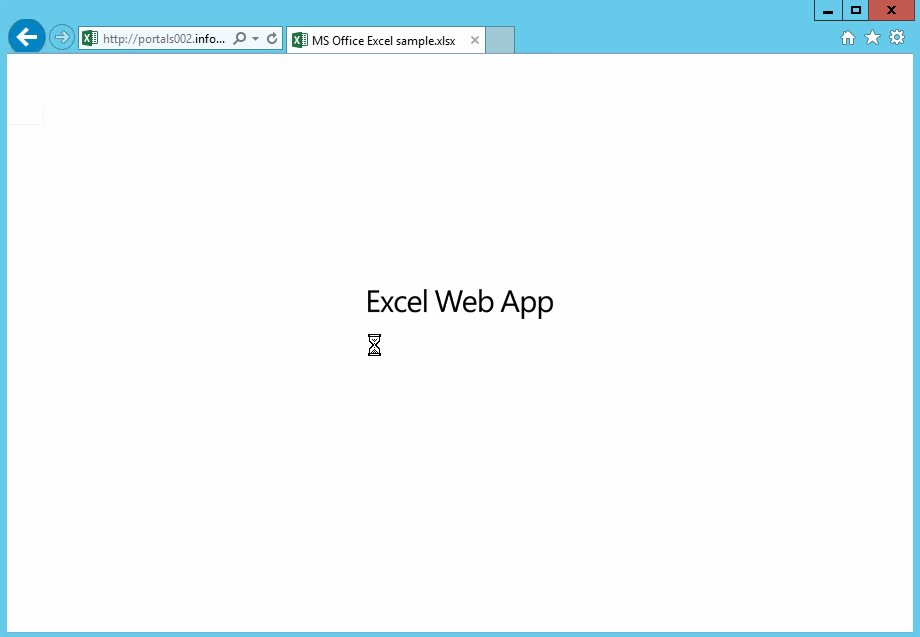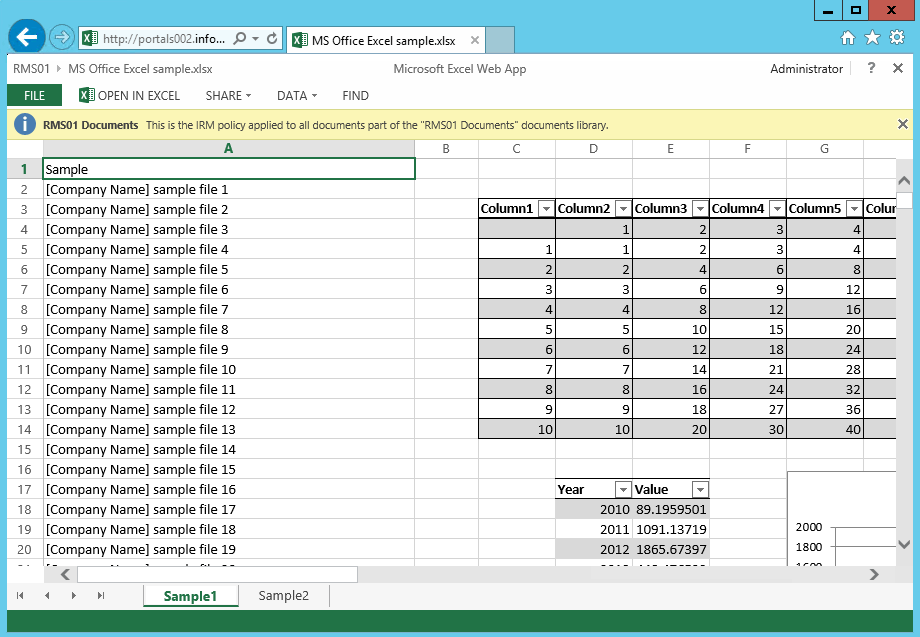
I am starting with a short update for those who don’t know the story with SharePoint 2013 Excel Services and Excel Web App (part of Office Web Apps Server 2013).
There are two Excel “flavors”: SharePoint 2013 Excel Services (available in SharePoint 2013 Enterprise edition) and Excel Web App (available in Office Web Apps Server 2013). These two Excel flavors offer different capabilities. The bad part is out of the box SharePoint allows only one of them to be used. You can control which Excel (SP Excel Services / Excel Web App) to be used for specific actions, but that is a farm-wide setting. You don’t have much flexibility.
For example, let’s say we have:
- a single SharePoint 2013 farm (the topology is not relevant);
- the SharePoint 2013 farm is linked to Office Web Apps Server 2013;
- the SharePoint 2013 farm will be used to host Business Intelligence site collections and also site collections with Libraries that have Information Rights Management (IRM) enabled;
Microsoft is explaining this in its support article.
“In SharePoint Server 2013 on premises, you could be using Excel Services in SharePoint Server 2013 OR Excel Web App (as part of Office Web Apps Server) to view workbooks in a browser window, depending on how your SharePoint environment is configured. “
“IMPORTANT: The decision about whether Excel Web App or Excel Services is used to display workbooks in a browser window applies to the entire SharePoint environment. You can’t have Excel Web App in one site and Excel Services in another. Contact your SharePoint administrator for more information about how your environment is configured.”
The SharePoint admins who configure the farms to support Business Intelligence features using Excel, usually configure them using:
Add-PSSnapin Microsoft.SharePoint.PowerShell New-SPWOPISuppressionSetting -Extension "XLS" -Action "view" New-SPWOPISuppressionSetting -Extension "XLSX" -Action "view"
What basically the above commands do is to change the default Excel behavior only for the View action. I call this a trick because these settings allow the Excel Services part of SharePoint 2013 to be used only for view mode, while Excel Web App (part of Office Web Apps Server 2013) will be used for the rest of the cases (edit, editnew, mobileView, embedview …).
However, Excel Services part of SharePoint 2013 will be farm-wide used for view mode, case in which you will miss functionalities like viewing IRM protected workbooks in browser.
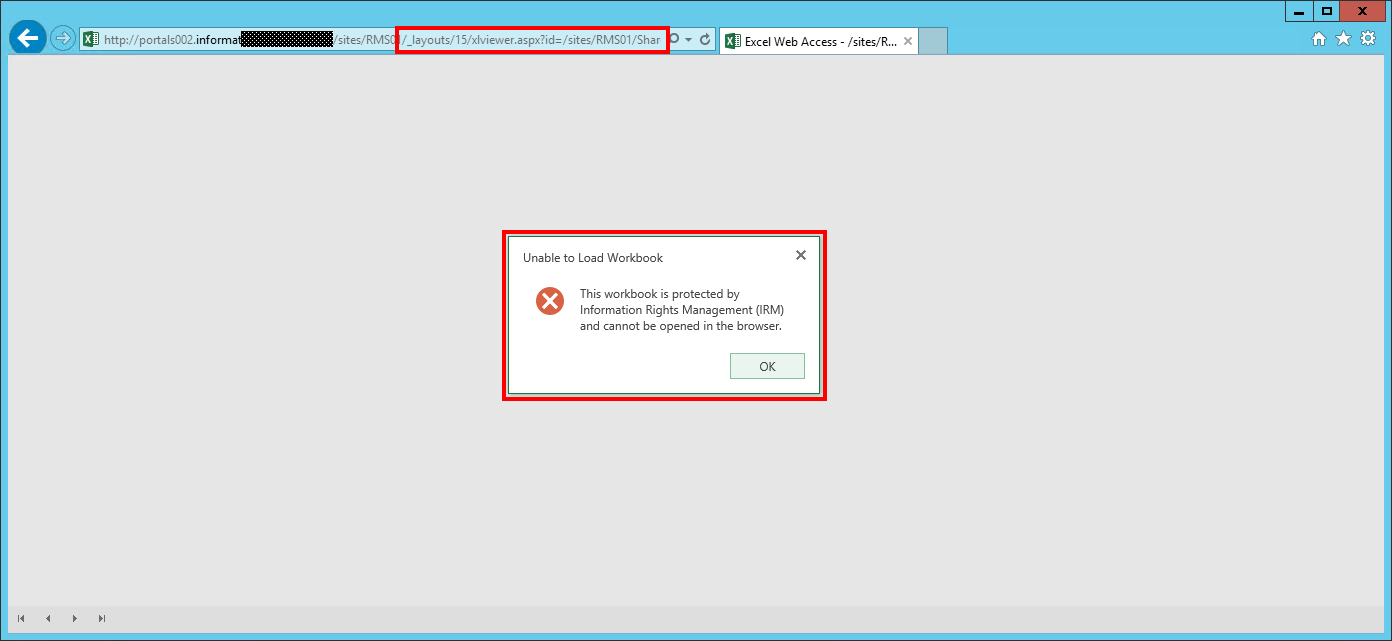
Unable to Load Workbook
This workbook is protected by Information Rights Management (IRM) and cannot be opened in the browser.
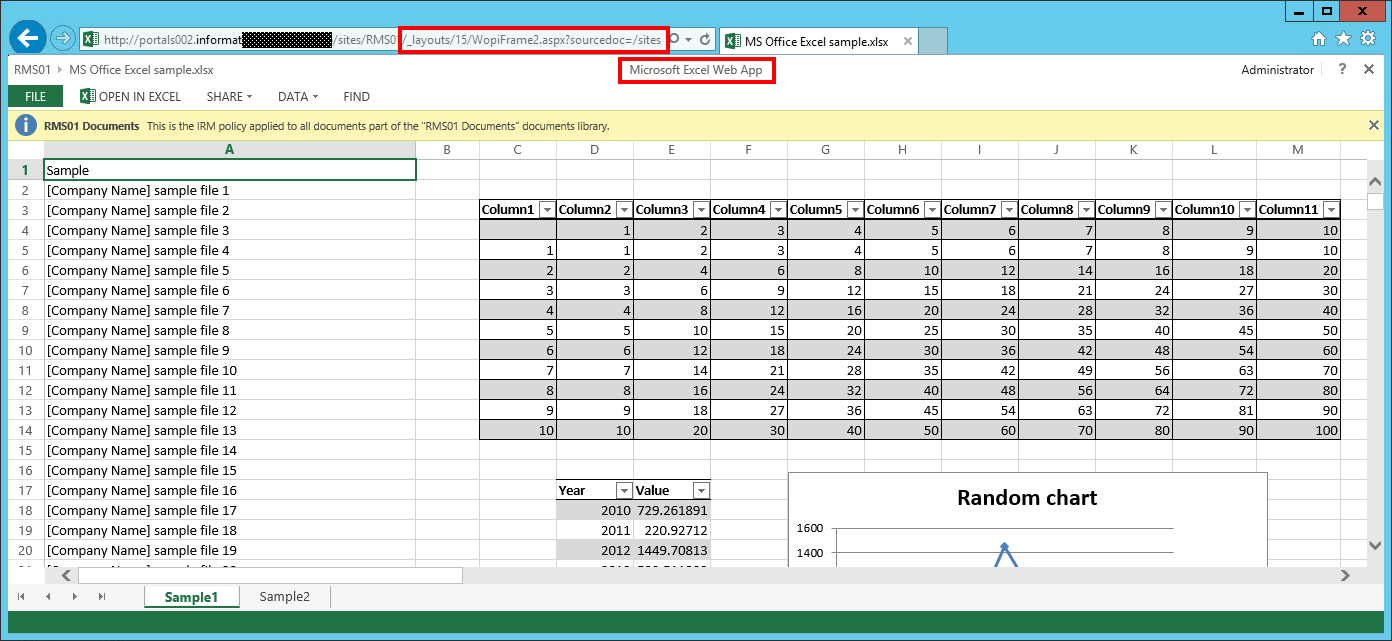
In fact, the document can be opened in the browser using Excel Web App if the URL is adjusted.
Replace http://[servername]/_layouts/15/xlviewer.aspx?id=/Documents/XYZ.XLSX with http://[servername]/_layouts/15/WopiFrame2.aspx?sourcedoc=/Documents/XYZ.XLSX).
To achieve this functionality I wrote an HttpModule that “intercepts” the URLs who contain xlviewer.aspx and redirects the request to the crafted WopiFrame2.aspx URL. In this way is possible to achieve a bit more extra flexibility in terms of controlling where to use Excel Web App (part of Office Web Apps Server 2013) on a farm configured to use SharePoint Excel Services as default.
The solution is available on GitHub.
The solution was developed as Web Application scoped feature. That means the extra flexibility in terms of the two Excel flavors applies to all the site collections within the Web Application where the “Excel Web App Redirecter” feature will be activated. The code I wrote can be forked or I can create branches for those who want to contribute and add a bit of extra functionality -> to make the feature granular up to SPWeb level. In my case, the solution works perfectly because all the IRM protected SharePoint libraries are hosted by site collections part of a specific SharePoint Web Application.
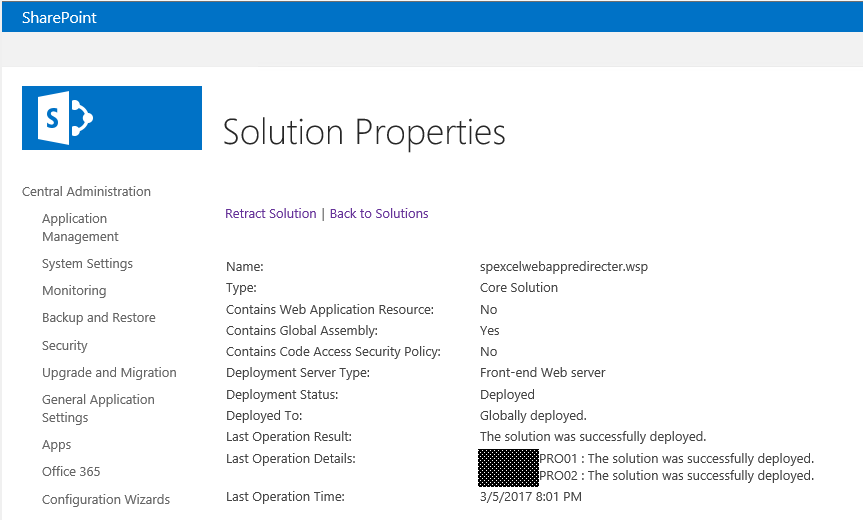
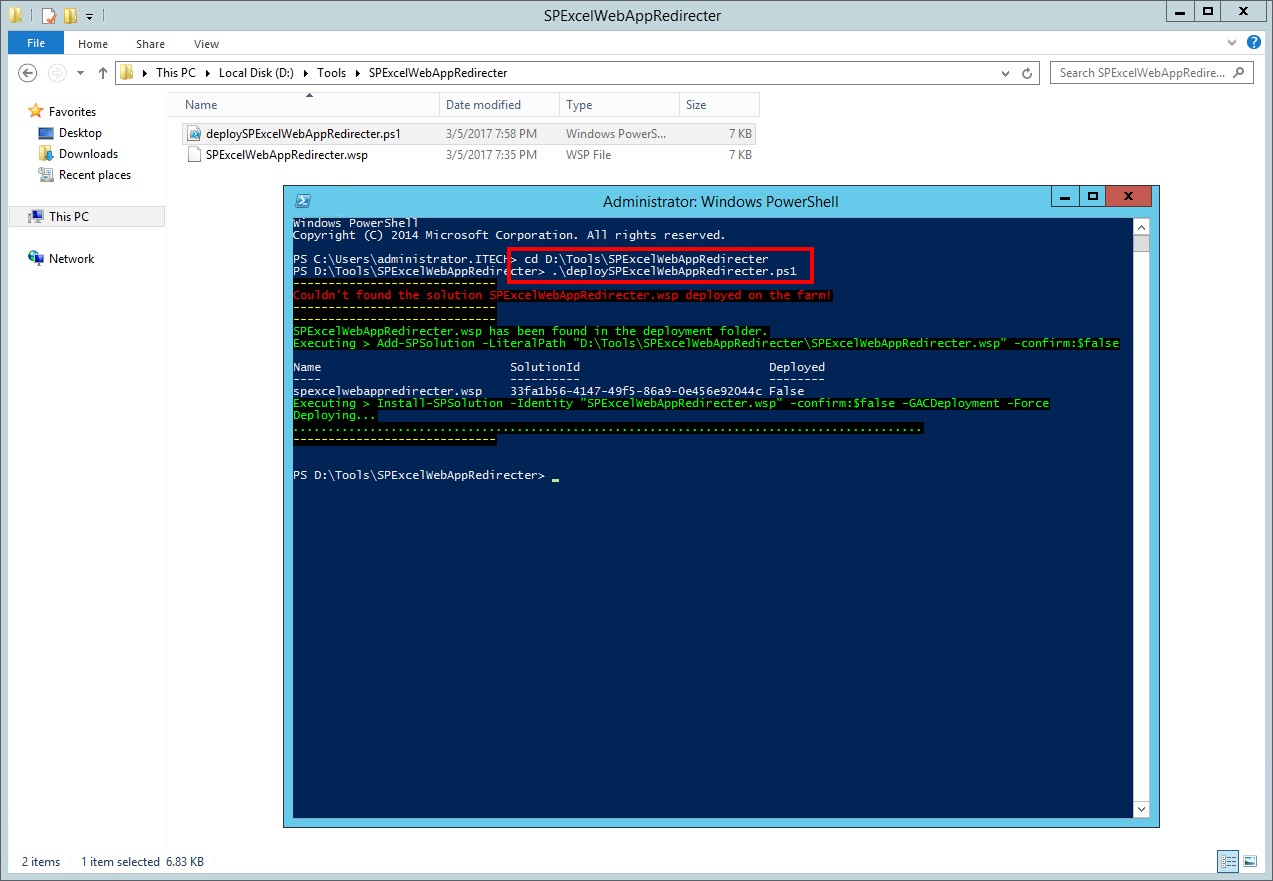
Let’s see step by step how to download and deploy the SPExcelWebAppRedirecter solution
- Download SPExcelWebAppRedirecter.wsp and deploySPExcelWebAppRedirecter.ps1 on one of your SharePoint servers (Web-Front or Application Server) and make sure you place both files in the same folder.
a
- Start the PowerShell console as Administrator and execute the deploySPExcelWebAppRedirecter.ps1 PowerShell script.
Please note the deployment duration will vary based on your farm topology. Please plan this deployment outside the production hours, because during the deployment IIS Application Pool recycle is performed.
aa
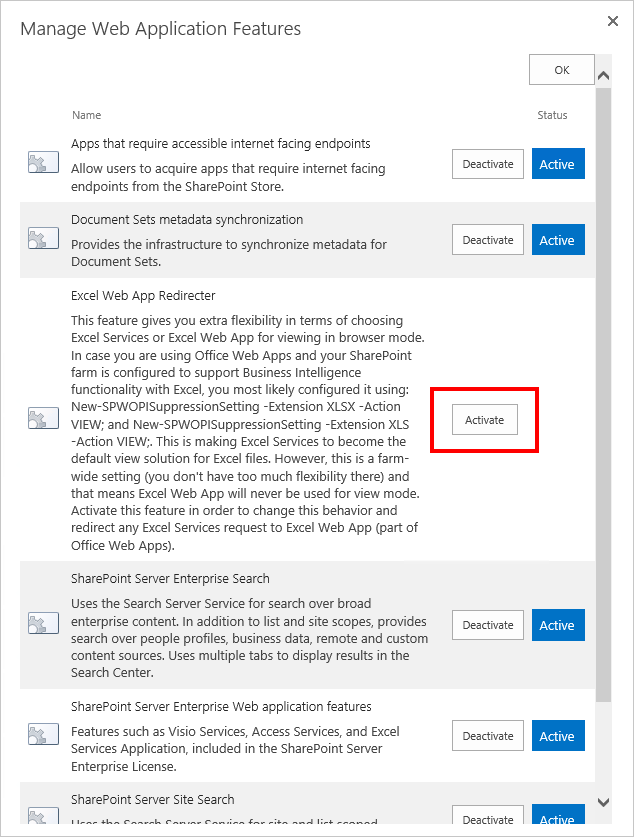
- Once the solution was successfully deployed, it is time to activate it to the SharePoint Web Application where you want the default Excel view to be handled by Excel Web Apps (part of Office Web Apps Server 2013).
a
- Once the feature is activated, all the site collections hosted by that SharePoint Web Application will have the default Excel view handled by Excel Web Apps.